For large teams working on complex game projects, tracking who made what changes becomes increasingly difficult. To keep things smooth and secure, implementing effective granular access control becomes essential for managing who can access what data and when. This systematic approach tracks and records the work done by each resource, and organizations have started investing greater resources in granular access control to ensure efficient team collaboration..
What is granular user access control?
Granular access control means providing differing levels of access to a system to specific users or groups. For a grid-like database, users are authorized to access and edit only specific tables or parts of tables.
Examples of user access rights:
- Read all data or part of the dataset
- Change account structure
- Change data structure
- Manage users and their rights
- Delete dataset or the whole account
While small-scale developers can use manual tracking systems, larger companies need granular access control for stability and efficiency. Companies like Gameloft have multiple offices that collaborate seamlessly through efficient granular access control mechanisms.

3 types of granular access control
1. Access control lists (ACL)
In access control lists, once a user has been authenticated, that user is free to access the system, independent of the fact of whether the user is listed under authorized users or the blacklist of the blocked users. This measure has downsides i.e. it ignores resources, actions, and the context when authorizing a user, considering only a singular dimension of the user. On the other hand, however; it is a very user-specific method.
2. Role-based access control (RBAC)
This method is predicated upon the particular set of roles a user embodies in the system. It is role-specific instead of being user-specific. Under RBAC, a user is granted various permissions against the number of roles assigned. The system lets the users define roles along with the associated permissions. These roles are then assigned to the users, which transitively grants permissions.
3. Attribute-based access control (ABAC)
The attribute-based Access Control allows the administrator to categorize information about the users to define a rule. The ABAC grants permissions to the users based on their attributes, instead of broadly defined roles. Attributes crunch any bit of information that correlates with a user, resource, target, object, and etcetera. This way, the ABAC makes it possible to corroborate attributes to define extremely targeted rules for the users. This way, the administrators can include extensive parameters to intricately manage the security system.
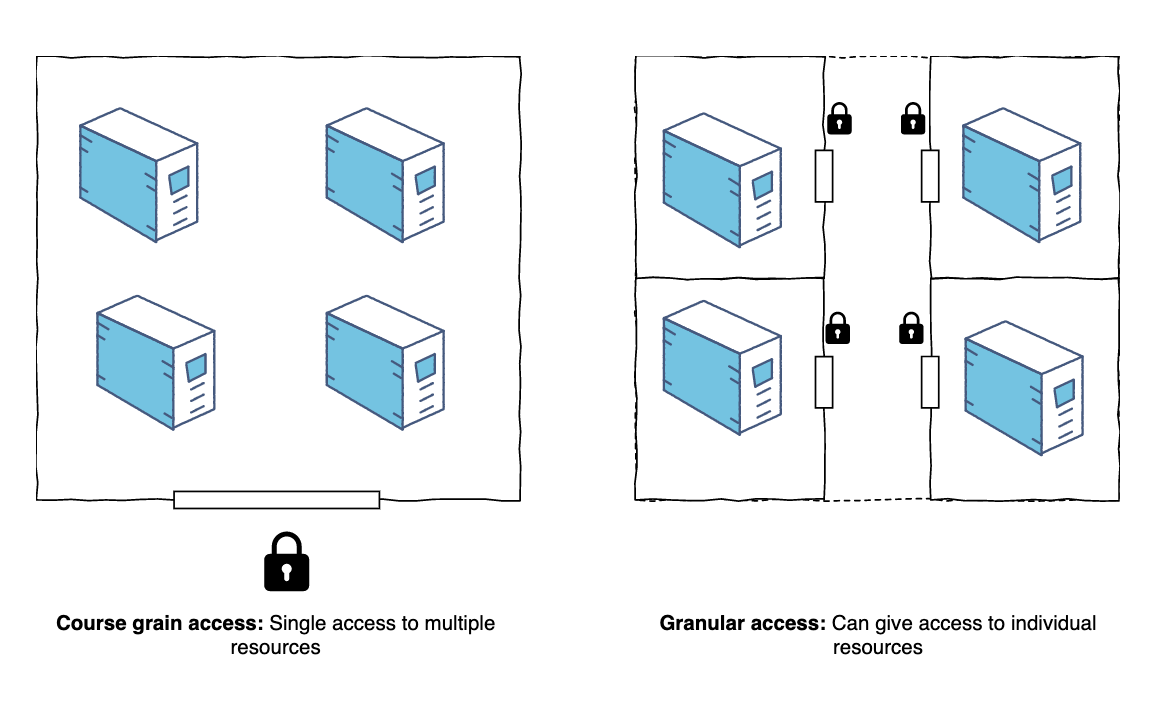
Why is granular user access needed?
To minimize security risks
The fundamental goal of granular access control is to mitigate the internal and external security risk of unsanctioned access to the physical and logical systems of any given organization. It is essential for any small to large-scale game studio to ensure that its security technology and access control policies protect any confidential information, which includes intellectual property as well as customer data.
Without granular access control, game companies would be left with no option but to provide full credentials to every resource at the company whether the resource is a Developer, a Designer or a Project Manager. This way it becomes extremely hard to track the users and their activities.
To prevent loss of data
When we speak specifically about the gaming industry, it has expanded manyfold in the last decade and with time has given rise to questions about consistency of data. Of great importance is how development teams can collaborate efficiently in real-time without latency and loss of data. With many developers, localization managers and translators having remote access, granular methods make it easy to manage individual authorization. Meanwhile, the administrator can alter the rules and user privileges instantaneously while protecting private data.
For seamless collaboration & remote work
Following the new trend of GaaS in the gaming industry, even the biggest game engines have now made a shift and invested heavily to create systems that allow seamless collaboration (such as Unity’s Collab). It helps control who can view or use resources in the computing environment of the company.
Since developers can access servers from virtually anywhere in the world, it becomes rather impossible to be suspicious of numerous IP addresses logging in the organization’s servers. In some systems, granular access control can simply limit the number of locations from where a server can be accessed to prevent any vulnerability.
For cost control
The old method of manually controlling permissions inflicts a sizable additional cost in terms of human resources. Even if the cost is not the stumbling block, any number of employees cannot be able to update and adjust the rules in real-time. Under the GAC, an organization can restrict access to the system without getting in the way of the users completing their tasks. This is a feature that services like Gridly or Unity Collab provide for game developers, hence resulting in an overall decrease in the cost of game production.
For localization
Localization requires a large team of staff that are not necessarily all employed by a game company. Localization managers, translators, content writers, voice-over artists are just some stakeholders to start with.
When implementing granular access control for game localization, establish a structured game localization process defining clear roles and responsibilities. This ensures access permissions align with workflow requirements.
For example, it’s essential for translators to:
- view the source text and all the target translations,
- be able to ask questions and leave comments on the text,
- edit only translations assigned to them (and, unfortunately, traditional spreadsheets do not fulfill this purpose – you need to create a separate document for each language pair).
If the game localization is not handled properly, deadlines could move and mistakes and data loss may occur. A system that provides granular user access facilitates the localization workflow by grouping people and granting them different levels of access.
For instance, a localization team working with the Chinese language, will only be able to access the part of the game target text to be translated into Chinese. Japanese translators may still be able to view Chinese translations and leave comments but they won’t be able to alter the strings in Chinese.
How to set up and review user rights in localization: a use case
We’ll take Gridly as an example, however this approach can generally be applied to any game localization project and system.
In Gridly, there are four default company roles:
- Owners: have full access to all company features including company management, billing, member management, and both CMS and TMS modules.
- Admins: have the same rights as Owners except for billing and some company management functions.
- TMS Manager: focused on Translation Memory System management with access to TMS features but limited CMS access.
- Users: have basic access to work with grids and databases in the CMS module.
Within the company, Owners and Admins can create new custom roles and assign different functions.
For example:
- Localization Manager who will be able to create, update and delete localization projects and grids.
- Translation Memory Manager who can import/export strings into a TM, clear all strings in a TM, etc.
- Translator who will have editing rights to the strings/columns with the target language and only the right to view or comment on the content in the source language or translated text into other languages.
- Moving further, with such a setup, the strings can be still localized and tested by a loc team, however, they can be pushed into the game by a Localization Producer or a user with publishing rights.
Using a handy game localization platform like Gridly could save your team from quite a few unwanted headaches. A service that allows you to easily translate, update and manage your game descriptions, in-game text and other metadata could save you hours of managing a team of translators and linguists.